Technical Overview
Liquid Technical Overview
Liquid is a sidechain-based, Bitcoin layer-2 settlement network linking together cryptocurrency exchanges and institutions around the world, enabling faster, more confidential Bitcoin transactions and the issuance of digital assets. Liquid is an implementation of Elements, an open source, sidechain-capable blockchain platform, based on the Bitcoin codebase.
Liquid provides Bitcoin exchanges and traders with a range of powerful features:
- Fast, Final Settlements: Bitcoin moved to the Liquid sidechain (Liquid Bitcoin, “L-BTC”) can achieve final settlement within two minutes.
- Confidential Transactions: Amounts and type of asset transacted are hidden by default on Liquid, keeping users’ financial data safe.
- Secure Tokenization: New tokens can be issued on the Liquid sidechain (Issued Assets) to represent fiat, securities, or other digital assets.
- Interoperability: One Liquid integration provides support for both L-BTC and Issued Assets. All tokens are based on the same standard, allowing users to take advantage of features such as atomic swaps and Bitcoin-style multisig.
Liquid is built using the open-source Elements code base. This is why you download the application from the Elements repository, execute commands against elementsd (daemon) and elements-cli (client), and edit things like the elements.conf config file.
Sidechain Basics
Liquid is a sidechain of Bitcoin that allows users of the Liquid Network to move Bitcoin between the two networks with a two-way peg. Bitcoin used in the Liquid Network is referred to as L-BTC, and each L-BTC has a verifiably equivalent amount of BTC secured by the Liquid members called functionaries.
A sidechain is a mechanism that allows tokens from one blockchain to be used securely in an independent blockchain which runs in parallel and uses a different set of rules, performance requirements, and security mechanisms. On a sidechain, one can move tokens back to the original chain through a two-way peg. Sidechains enable new functionality that may have security trade-offs or as a way to test new features that may not be ready for use on the parent blockchain.
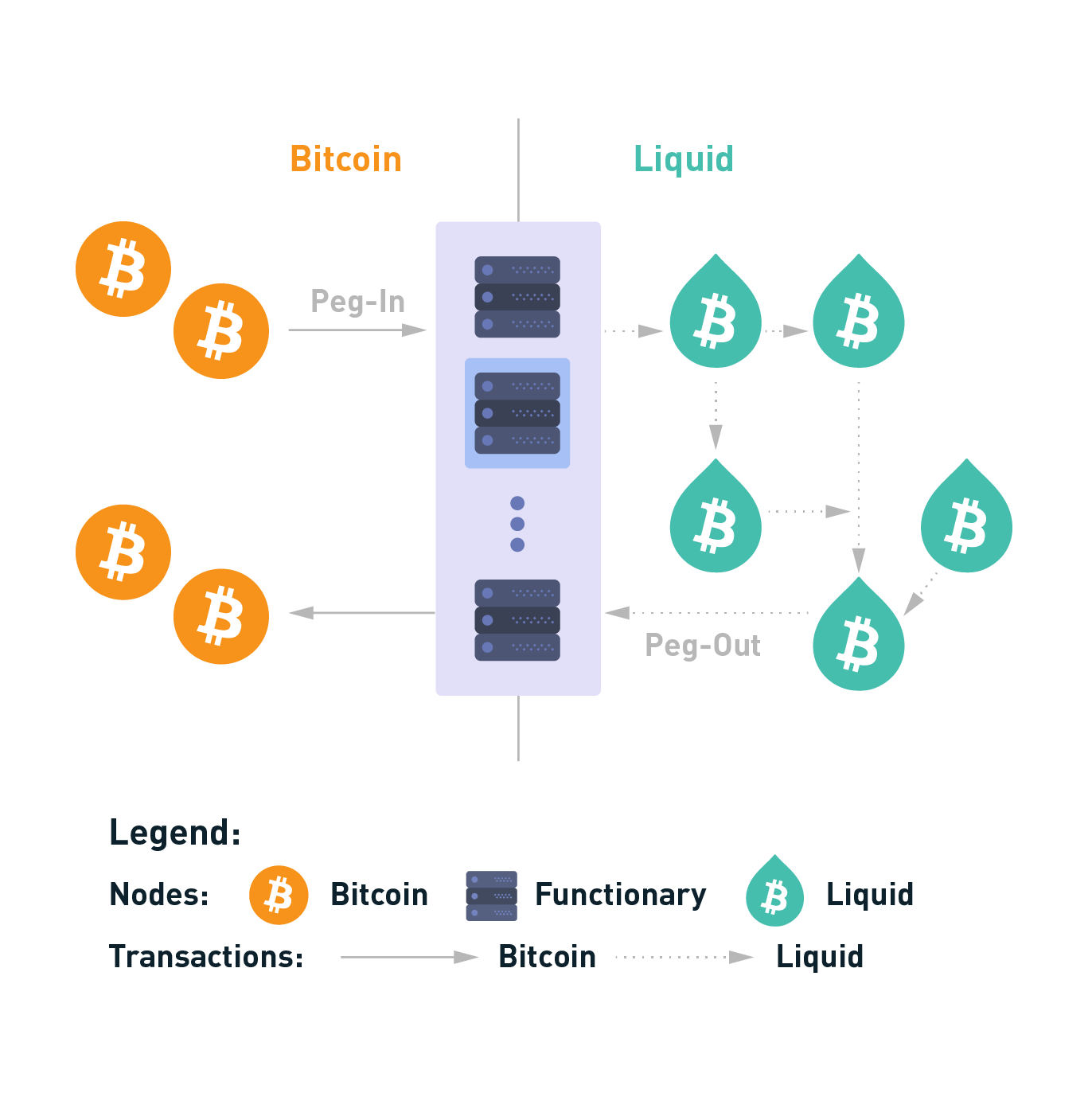
Network Roles
The Liquid Network is operated by members - large exchanges, financial institutions, and Bitcoin-focused companies - geographically distributed all over the world. Blockstream serves only as a technology provider. With no single entity in control and a geographically diverse membership, there is no single point of failure.
Liquid uses an approach to consensus called Strong Federations. A Strong Federation removes the need for costly Proof of Work mechanisms and replaces it with the collective actions of a group of mutually distrusting participants called functionaries.
Functionaries
These functionaries each serve two roles on the network - as blocksigners they operate the Liquid sidechain, and as watchmen they secure Bitcoins held by the Network.
Block Signer
Liquid’s block generation occurs every minute. This means that Liquid’s block generation is more consistent than Bitcoin’s (which has probabilistic generation). Block signers keep track of the block height they have signed along with its parent and refuse to sign blocks that would result in a reorganization of more than one block. Once a block has been created, its parent block will never be reorganized from the longest chain, which is why Liquid transactions can be considered final once they receive two confirmations. Liquid transactions will settle between two and three minutes when the network is functioning normally.
Liquid’s federated model requires blocks to be signed by at least two-thirds of all block signers. Block signers take turns proposing a new block every minute in a round-robin fashion, and other functionaries sign that block after validating its contents. Blocks will be created every minute when the network is functioning normally. However, it is possible that network instability or missing functionaries can result in some block rounds being missed. When fewer than one-third functionaries are offline, the network can continue. When the offline functionary becomes the block proposer of a round, that round will fail, which will result in no block being created during that interval.
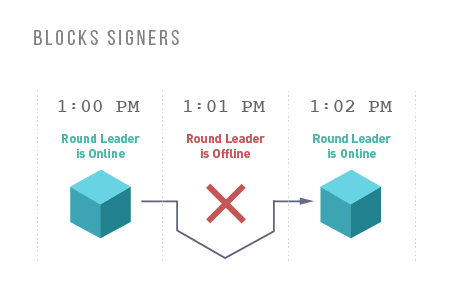
If one-third or more of the functionaries are no longer operating, blocks will no longer be signed and the Liquid blockchain will be frozen until at least two-thirds of the functionaries come back online. Once a quorum of functionaries are communicating, block creation will resume.
Watchmen
One of the two duties of a functionary is to serve as a watchman. In this role, the functionary is responsible for managing and securing the Bitcoin held by the federation.
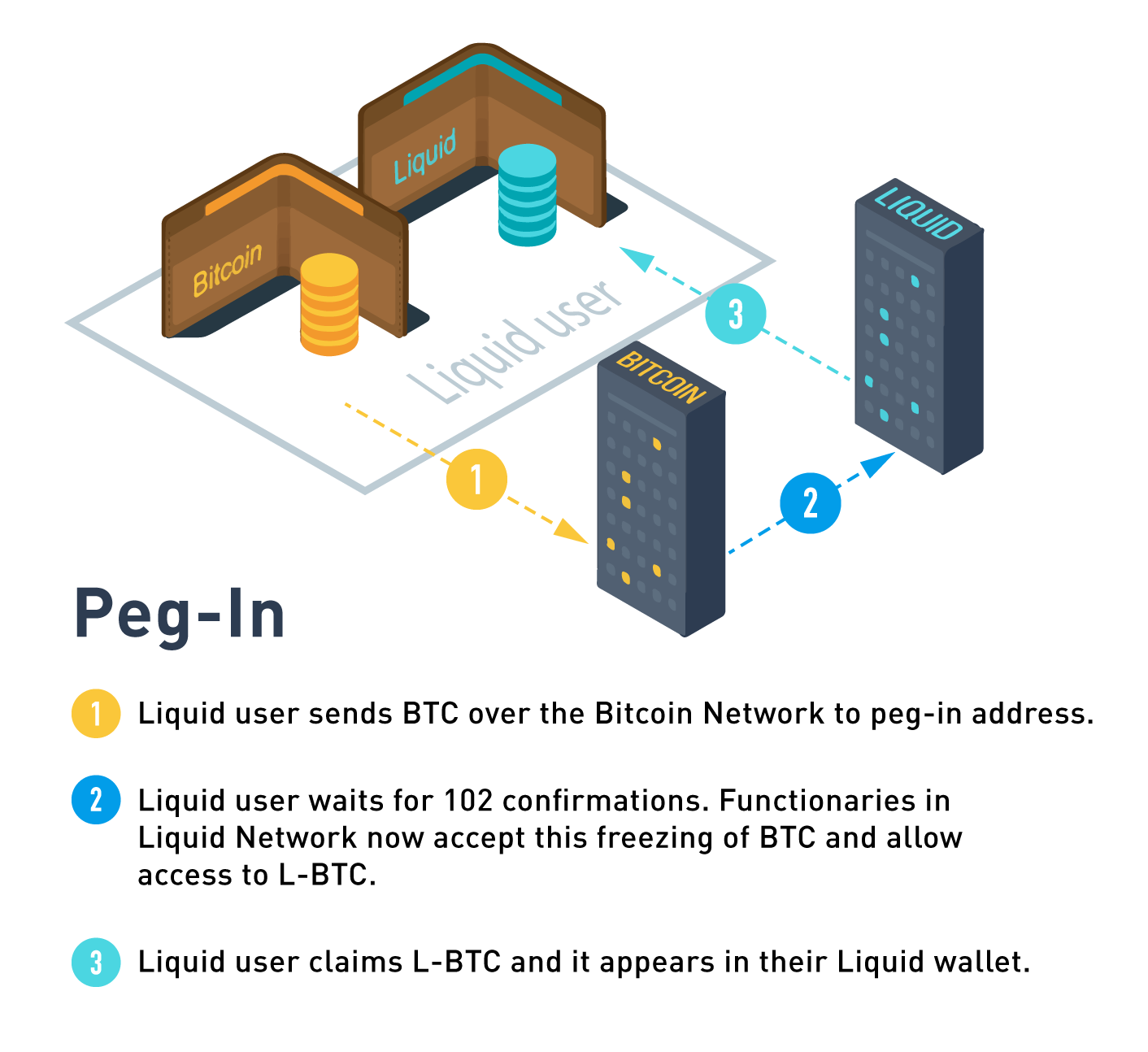
Peg-in (Bitcoin to Liquid)
Moving funds from Bitcoin to Liquid is called a peg-in; a Liquid user sends bitcoin to an address generated by the Liquid client software and then creates a peg-in transaction to claim its equivalent Liquid Bitcoin (L-BTC) from the Liquid Network.
A peg-in transaction requires 102 confirmations on the Bitcoin network before the funds can be claimed on the Liquid Network. This high level of security is required to protect all participants’ funds in the event of a large block reorganization of the Bitcoin blockchain.
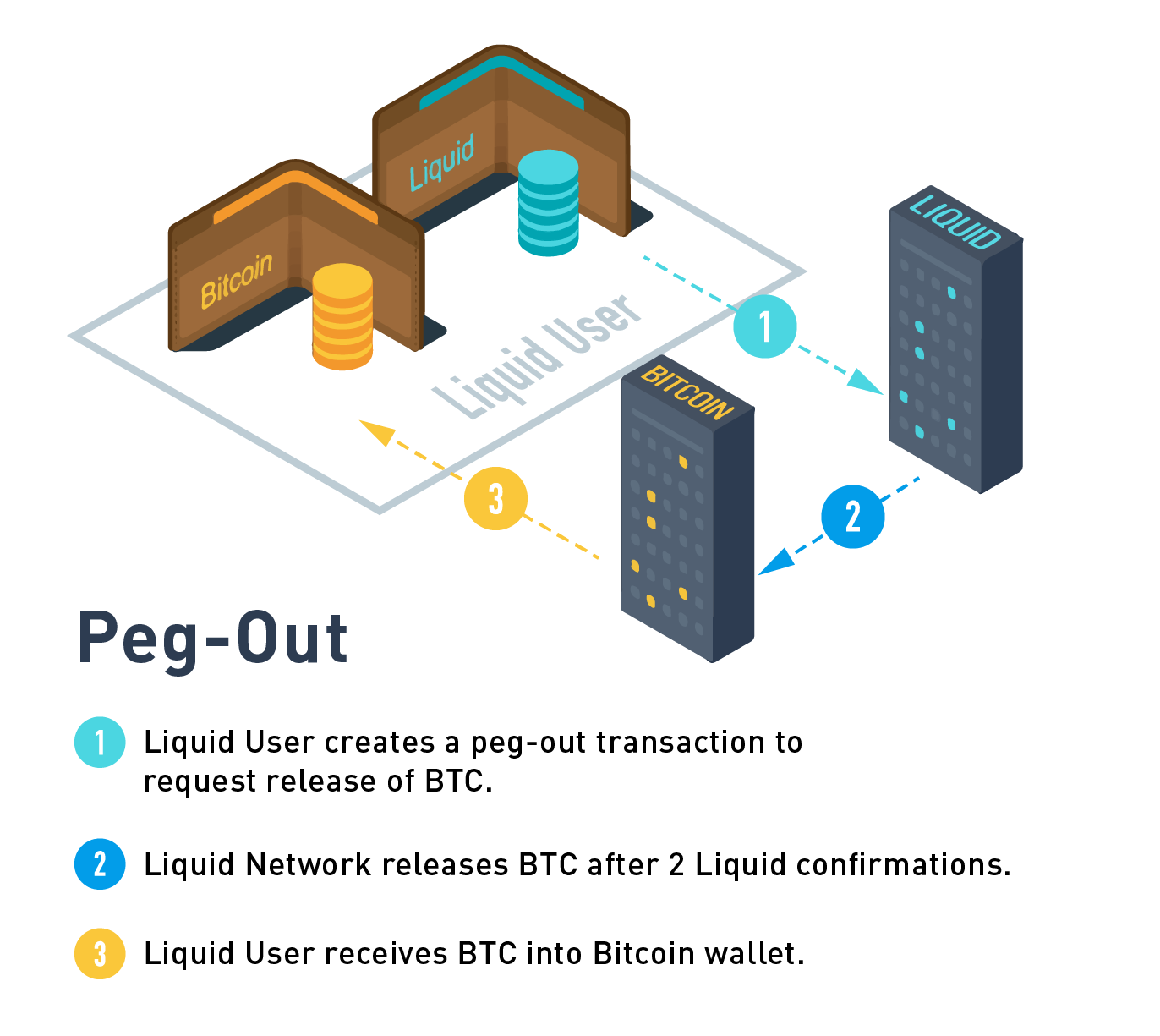
Peg-out (Liquid to Bitcoin)
The peg-out process moves funds from Liquid back to the Bitcoin blockchain. These transactions are processed by the watchmen in batches, where each peg-out round takes an expected time of ~17 minutes to complete.
Peg-out processing time
The peg-out process is non-deterministic with an expected processing time of 11 to 35 minutes depending on the network conditions, such as watchman status when user peg-out was initiated and number of other peg-outs pending to process.
For added security, the watchmen will only send bitcoin to an address under the control of an authorized user. This is done through the use of a Peg-out Authorization Key (PAK). Functionaries control a list a of PAKs that can be updated throughout the network operation to determine which users are authorized to make a peg-out transaction. In order to protect Liquid from unauthorized withdrawals, it takes three days to update the PAK list. This allows the network to detect an attacker that is able to compromise a set of functionaries before the attacker is able to make a withdrawal to their own wallet. PAK entries are linked to a BIP32 (Hierarchical Deterministic) Wallet owned by the user. Liquid users create a peg-out transaction proving that their address is derived from one of the PAK entries without revealing any additional identifying information.
Emergency Recovery Procedure
Due to the use of multisig, the watchmen require a greater than two-thirds threshold to spend funds in the Liquid Network which provides sufficient security for Byzantine fault tolerance.
If Liquid used multisig alone, then in the unlikely event that one-third or more of the network was unable to continue operating, the network would stall and the funds held would be locked up forever. To avoid this, the federation’s multisig wallet also incorporates a timelock, which ensures that all funds held by the Liquid Network are accessible by a set of three emergency keys if the network has been non-functional for an extended period of time.
Hardware
The functionary server itself consists of two components - the host server and a key storage module. The host is a standard server that is used to run a full Bitcoin and Liquid node and communicates with the other functionaries over Tor. Tor is used by the functionaries to ensure that all communications between the functionaries do not contain IP addresses which could lead to members of the network being subject to denial of service attack, and to avoid disclosing the physical location of the servers. The host is responsible for proposing blocks and staying in sync with each of the other functionaries. Attached to each host is a key storage module that is connected via a limited interface. No block signing or watchman key material is ever stored on the host to limit the ability of a remote attacker compromising the network. The host is configured to only allow incoming SSH connections when a button is pressed which allows for authorized users to connect and perform updates to the software or PAK list. This protection means that physical access to the functionary server is required to perform any changes.
The key module does additional validation before signing blocks or creating Bitcoin transactions. The key module also ensures that Bitcoin spent from the network only is spent to a set of authorized users.
It is recommended to have physical access restricted to the functionary server in order to avoid tampering. The functionary server must be installed on a private network with unrestricted outgoing connections. Liquid wallets and transactions are managed through separate Liquid node software that will connect directly to your functionary.
Participants
The Liquid Network consists of a fixed group of functionary members that is defined at launch. Members without functionary hardware connect to the Liquid Network by using pseudo-functionary nodes that connect to all functionaries. Participant members can perform peg-ins, peg-outs, send Liquid transactions and fully validate the Liquid chain, without playing a role in securing the network.
General Public
Anyone can participate in the network by running a full node. These full nodes connect to the Liquid network via bridge nodes that are run by Functionaries and Participants members. Liquid full nodes allow users to trustlessly self-validate the chain just like with the Bitcoin Network and give its user free range ability to peg-in to the network, perform confidential transactions and make full use of the Issued Assets functionality.
Who can peg out?
The general public does not have the ability to independently peg-out of the network, which means they require from a Functionary or a Participant member to convert L-BTC back to BTC.
| Functionaries | Participants | General Public | |
|---|---|---|---|
| Secures the Network | YES | NO | NO |
| Peg-in (BTC to L-BTC) | YES | YES | YES |
| Peg-out (L-BTC to BTC) | YES | YES | NO |
| Send Confidential Transactions | YES | YES | YES |
| Issue Assets | YES | YES | YES |
Confidential Transactions
One of the main features of Liquid is its default use of Confidential Transactions. Confidential Transactions on Liquid allows any two parties to transact without anyone else being able to view the asset and amount transacted, not even the Liquid Federation members and functionaries.
You can read about Liquid's confidential transactions here.
Asset Issuance
Liquid allows for users to create and transfer other assets using a feature called Issued Assets. These assets can enable applications such as tokenized fiat, tokenized non-BTC cryptocurrency, digital collectibles, reward points and attested assets (e.g. gold coins).
You can read about Issued Assets on Liquid here.
Additional resources
- The Liquid white paper has more technical information on the network's operation, confidential transactions, and issued assets.
- Elements Github repository
- Liquid Network end user FAQs
Updated 6 months ago